Blockster Labs has been featured by Code for GovTech (C4GT) in their Org Spotlight series! Click here to learn more.
Blog 2
Self-Sovereign Identity: How W3C Verifiable Credentials (VC) Work: Part 1 – VC Issuance
SSI space has moved a long way. The concepts of SSI, Decentralized Identity and verifiable credentials (VC) have been explored by many forward thinkers across the industries.

SSI space has moved a long way. The concepts of SSI, Decentralized Identity, and verifiable credentials (VC) have been explored by many forward thinkers across the industries.
There is enough material available online to understand the concepts of SSI and the steps involved in VC issuance, verification, and revocation. Still, we find it a bit tricky to consume them as is.
Hence, we thought of creating a series of blogs to make it easy for a SSI developer to dive into the creation, issuance, verification, and revocation of a VC. This article is to explain in a more granular way on what actually happens under the hood when VCs are issued and what makes VCs verifiable.
To make the article comprehensive, let’s have a quick recap of DID and VC. This article is not boxed to a framework or library say Hyperledger Indy and is based on W3C standards for Verifiable Credentials.
DID (Decentralized Identifier)
It is essential that all the entities (Issuer, Verifier, Holder) which are part of the Verifiable Credential ecosystem will have their unique decentralized Identifier or DID.
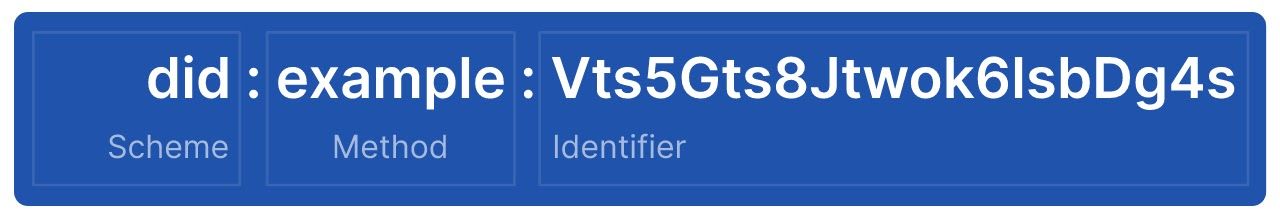
DID is a globally unique persistent identifier that does not require a centralized registration authority. Because it can be generated by anyone and/or is optionally registered cryptographically onto a verifiable data registry such as a DLT/Blockchain or a traditional database.
Example of a DID:
VC (Verifiable Credential)
Verifiable Credential is a digital credential that comes with Cryptographic power which makes it tamperproof, secure, and verifiable.
Lifecycle of a Verifiable Credential
A verifiable credential goes through four different stages
It is essential that all the entities (Issuer, Verifier, Holder) which are part of the Verifiable Credential ecosystem will have their unique decentralized Identifier or DID.
DID is a globally unique persistent identifier that does not require a centralized registration authority. It can be generated by anyone and/or is optionally registered cryptographically onto a verifiable data registry such as a DLT/Blockchain or a traditional database.
Depiction of credential issuance
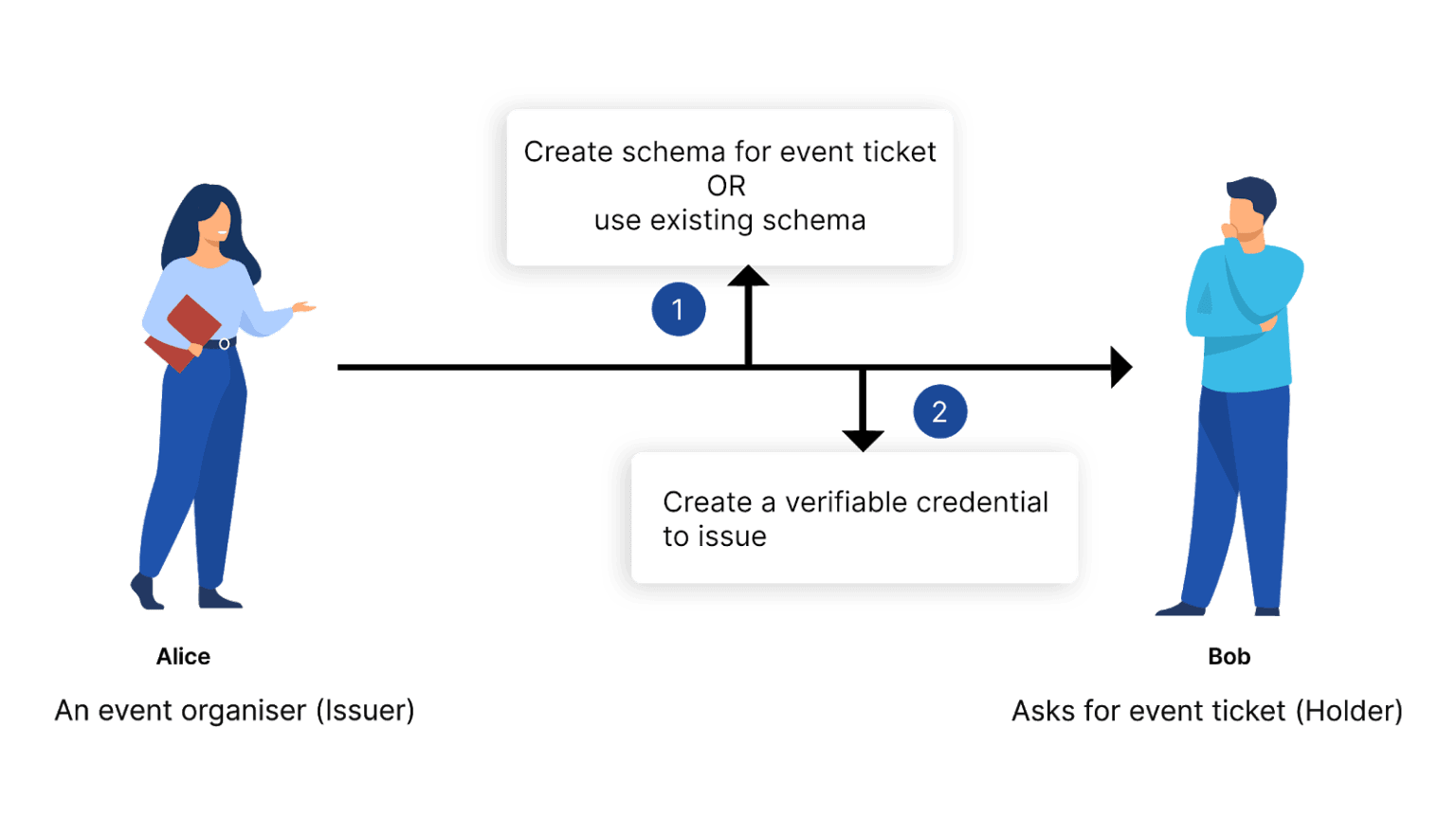
Before issuing a Verifiable Credential Issuer needs to write the credential schema also called a template or JSON schema on the ledger. This credential schema guarantees the structure and by extension the semantics, of the set of claims comprising a Verifiable Credential. A shared Credential Schema allows all parties to reference data in a known way.
There can be four viewpoints for a credential schema:
Features of a Schema
Follow for example of a JSON Schema as per W3C standard can be found here:
An Issuer can either use the existing Schema or create a new one and Issue credential
When an issuer creates a verifiable credential, it contains the following information –
So now that you’re familiar with how W3C verifiable credentials (VC) work, watch out for our next blog to get the details of what goes to the ledger in the credential issuance process.
Write to us at info@blockster.global if you have a query or to get more information on the subject.